When a suspicious domain like example.com appears in phishing or malware alerts, quickly assessing its full DNS footprint is critical. Running individual queries for each record type is slow and inefficient.
Silent Push PADNS solves this by delivering an instant, aggregated view of all raw DNS records (A, AAAA, CNAME, MX, NS, SOA, TXT) for the domain and its subdomains, directly inside Total View. Toggle Domain Wide View to include the entire hierarchy (blog.example.com, api.example.com, etc.).
Available for domains and IPv4 addresses, PADNS instantly reveals:
Misconfigurations (e.g., outdated MX records)
Risky infrastructure (e.g., high-risk nameservers)
Subdomain takeover risks (dangling records)
Fast-flux or high IP/ASN diversity
Community users get raw PADNS data for free. Enterprise users gain IOFA™ threat-feed enrichment. One click pivots to full DNS Data for advanced filtering, no extra queries needed.
Fast, complete, actionable DNS intelligence in a single view.
How It Works
The PADNS view uses Silent Push's PADNS to aggregate passive DNS data from our global collection, creating datasets optimized for threat intelligence. It reflects queries such as IP hosting a domain or Domain Name Server Changes, presented in Total View with risk scoring and navigation options.
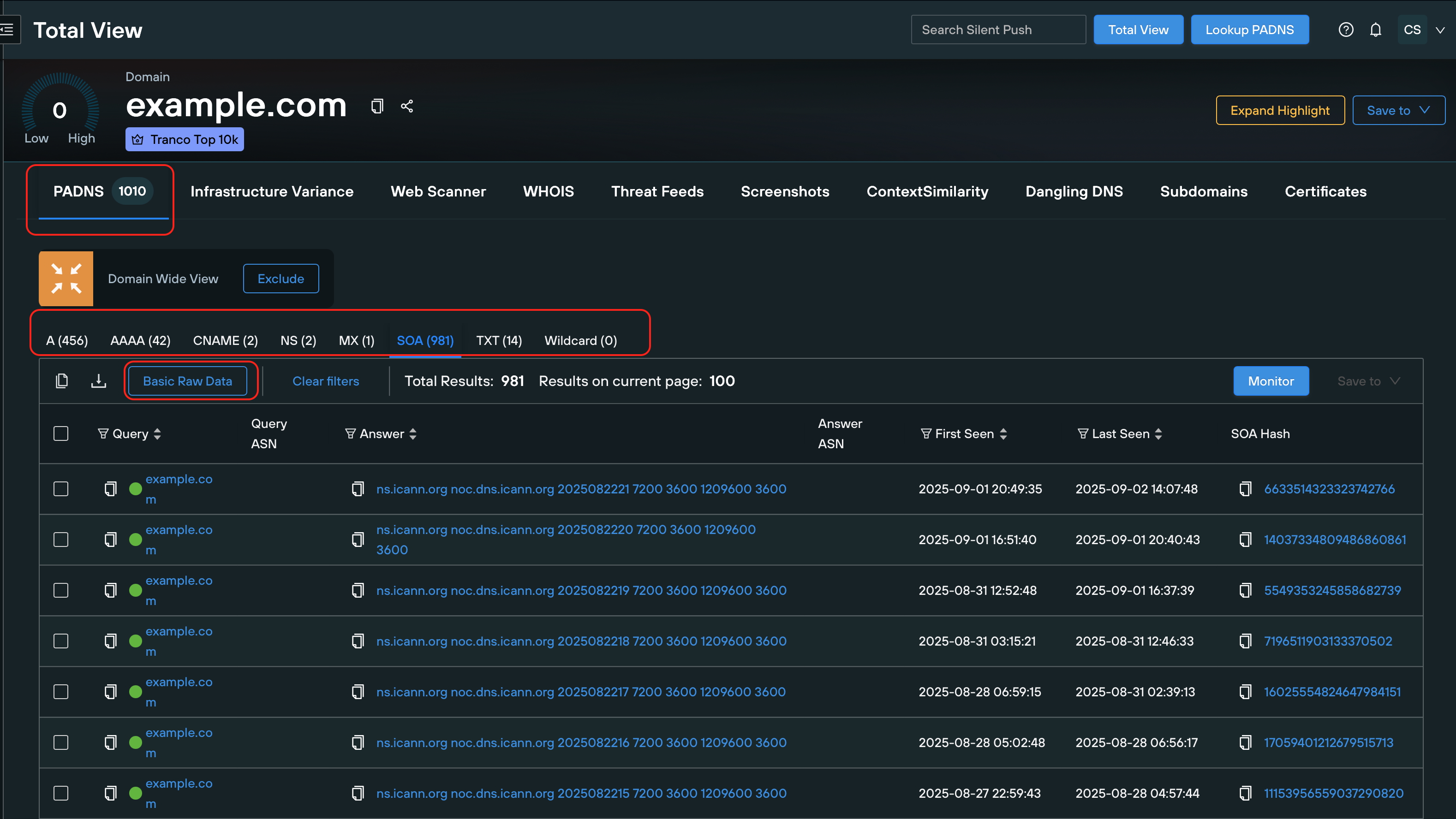
Counts (e.g., 456 A, 42 AAAA) appear at the top, followed by a filterable table showing queries (e.g., example.com), answers (e.g., ns1.scann.org), timestamps, and ASNs. The Domain Wide View includes subdomains to highlight issues such as TXT SPF inconsistencies, indicating potential spoofing risks. Forward lookups connect to IP diversity for historical analysis; reverse data identifies shared infrastructure. All data is timestamped (e.g., First Seen 2025-09-01) for precision.
The section displays counts and details for these records across the domain and subdomains. A record, for example, derives from a forward lookup, such as IP hosting a domain, listing associated IPs with timestamps. Results may include three A records, one MX record, and two TXT records, highlighting server connections, email setups, and security policies. This helps detect anomalies, such as an unfamiliar NS record that may indicate misconfiguration or compromise.
Generate a Set of Results
Enter a domain (e.g.,
example.com) in the search bar to open Total View, and scroll to the PADNS view. Record counts are displayed at the top, with a results table below.Activate Domain Wide View to include subdomains. Apply filters by record type (e.g., NS only) or timeframe as needed.
Example
Query
example.comin PADNS: Aggregated records show 456 A records resolving to IPs like 203.0.113.5 (timestamped 2025-09-01), two NS entries forns1.scann.org(ASN 12345), and a TXT with SPF:v=spf1 include:_spf.example.com -all.Domain Wide View adds subdomains:
www.example.comCNAME toblog.example.com(AAAA: 2606:4700::1111), MX formail.example.com(priority 10), and SOA serial 2025090201 indicating a recent update. An NS shift to AS207713, with first/Last Seen dates (2025-08-31 to 2025-09-02), may indicate flux activity.
Tab in Action
A Record (Address Record)
Definition: Maps a domain or subdomain (e.g., www.example.com) to an IPv4 address (e.g., 192.168.1.1), which is the server’s numerical location.
Purpose: Provides the primary IP address for domain resolution, ensuring traffic reaches the correct server.
Example: An A record for blog.example.com pointing to 203.0.113.5 directs traffic to that server.
AAAA Record (Quad-A Record)
Definition: Maps a domain or subdomain to an IPv6 address (e.g., 2001:db8::1), supporting modern networks with larger address spaces.
Purpose: Enables IPv6 connectivity for domains, accommodating the growing number of Internet devices.
Example: An AAAA record for shop.example.com pointing to 2606:4700::1111 routes traffic to an IPv6 server.
CNAME Record (Canonical Name Record)
Definition: Aliases one domain or subdomain (e.g., fun.example.com) to another (e.g., www.example.com), sharing the same target configuration.
Purpose: Simplifies management by linking multiple names to a single address, reducing redundant IP records.
Example: A CNAME for test.example.com pointing to www.example.com directs traffic to the same server.
MX Record (Mail Exchange Record)
Definition: Specifies the mail servers responsible for receiving email for the domain (e.g., mail.example.com).
Purpose: Directs email traffic to the correct server, essential for email functionality and security checks.
Example: An MX record for example.com, pointing to mail.example.com with priority 10, handles incoming emails.
NS Record (Name Server Record)
Definition: Identifies the name servers that manage the domain’s DNS records (e.g., ns1.example.com).
Purpose: Indicates which servers hold the authoritative DNS data, critical for domain resolution and stability.
Example: An NS record for example.com listing ns1.example.com shows the managing server.
SOA Record (Start of Authority Record)
Definition: Provides administrative details about the domain, including the primary name server, contact email, and DNS update parameters (e.g., serial number, refresh interval).
Purpose: Acts as the master record, ensuring consistency across DNS servers and tracking updates.
Example: An SOA for example.com might list ns1.example.com as the primary server with a serial number of 2025090201 (updated 2025-09-02).
TXT Record (Text Record)
Definition: Stores text information associated with the domain, often used for verification or security settings (e.g., SPF or DKIM codes).
Purpose: Supports domain Authentication, spam prevention, or custom data, enhancing security and trust.
Example: A TXT record for example.com might contain v=spf1 include:_spf.example.com -all to define email sending policies