The Silent Push Chrome Extension extends the Silent Push platform, providing comprehensive intelligence directly in your browser. This enables rapid analysis of indicators of compromise (IOCs) encountered on SaaS platforms and in intelligence reports without maintaining an active session on the full platform. The extension delivers prompt insights and Actionable Intelligence to support informed decision-making.
Installation
Installation is straightforward for Chrome users:
Navigate to the Chrome Web Store.
Select Add to Chrome and approve the required permissions.
Locate the Silent Push icon (a shield emblem) adjacent to the browser's address bar upon completion.
Activate the icon, then authenticate with your Silent Push credentials to enable full functionality.

Usage
The extension is engineered for ease of use, offering three primary engagement methods:
Identify an IOC, such as a domain, on a webpage; select it, right-click, and choose Scan Indicator.
For targeted analysis, activate the icon, input the indicator (domain, IP, or URL), and initiate the scan.
To assess an entire page, select Collect DNS Data. This feature automatically identifies all domains, IP addresses, and URLs, provides risk scoring (including IOFA feed matches via Threat Check for instant high-risk flagging), detailed overviews, and options for further investigation or feed integration.
Regardless of the method, the extension leverages Silent Push's extensive data sources to furnish contextual information expeditiously.
Features
The user interface is intuitive, featuring organized tabs and actionable elements. Key functionalities include:
Total View: Highlights of what Silent Push intelligence on the indicator encompasses, including metrics such as DNS entropy, age scores, nameserver reputation, and threat feed associations. This view integrates Threat Check to instantly alert you when an indicator appears on an IOFA (Indicators of Future Activity) feed, enabling quick triage without diving into individual investigation tabs.
Live Scan: Initiate real-time examination of an IP, domain, or URL, including screenshot acquisition for evidentiary purposes. This is particularly useful for confirming active threats.
Web Scanner: Perform targeted scans across web-based data sources, enabling the identification of web-related indicators and potential exposures in real-time.
Feed Scanner: Query threat intelligence feeds directly to assess indicators against known malicious datasets, providing matches and enrichment from both production and draft feeds.
Save To: Capture and organize indicators into feeds for sustained analysis or distribution. Options include saving to existing feeds, new feeds, existing draft feeds, or new draft feeds, with support for bulk operations on selected IOCs.
Exercise
To familiarize yourself with the extension, complete this guided exercise, which uses a Silent Push blog article on emerging malware.
Open the Silent Push blog article on CountLoader, which examines a novel malware loader distributed in various configurations.
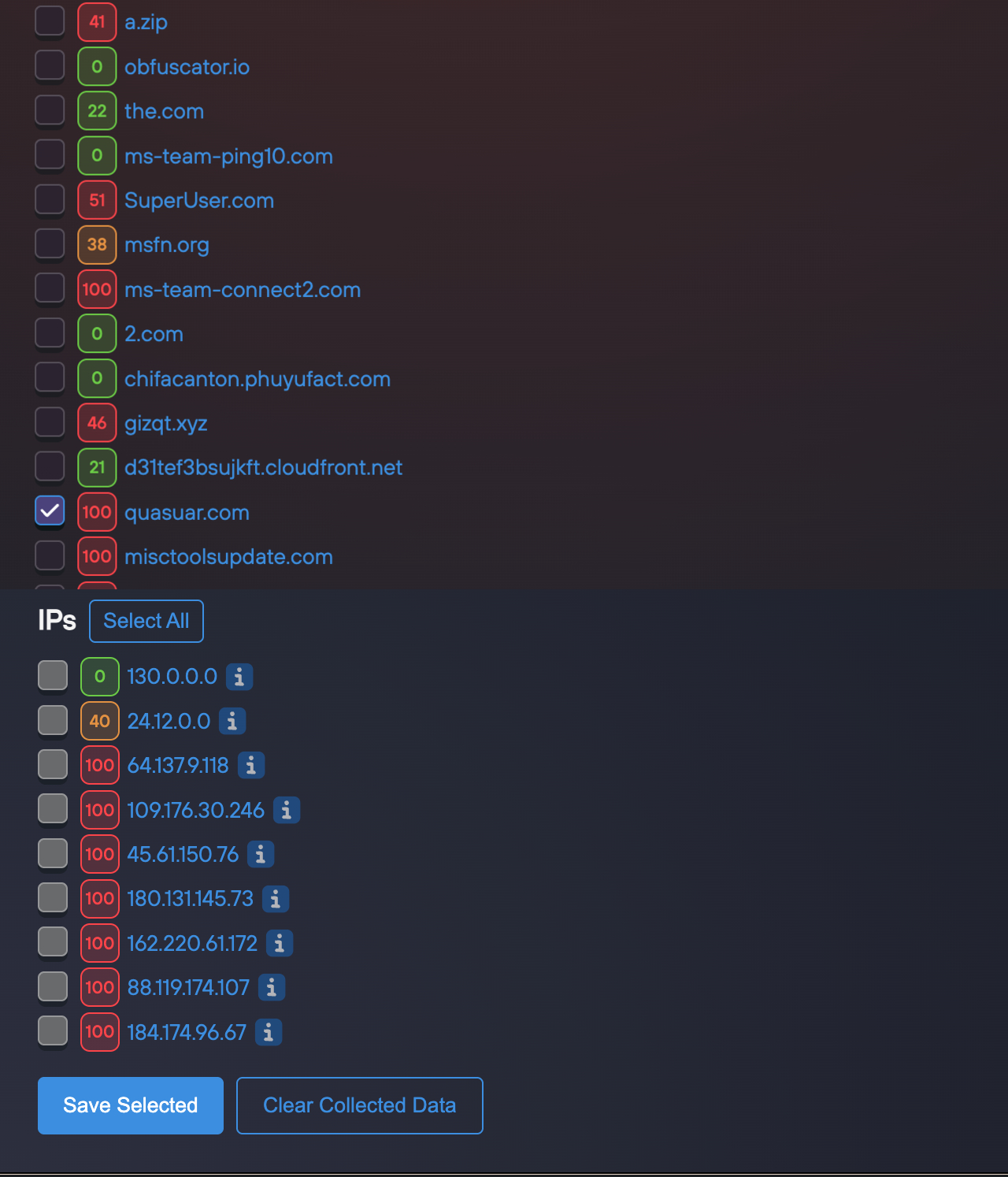
Locate the reference to "quasar[.]com" (a domain associated with command-and-control activities). Select it, right-click, and select Scan Indicator. Open the extension using the icon.
Review the synthesized intelligence, including strike score (approximately 100%), threat feed correlations (e.g., over 100 matches), Whois information (e.g., Namecheap registrar, creation date circa 2025-03-04), and supplementary details such as VirusTotal notations or ASN analyses. Visual representations of entropy and reputation scores provide a comprehensive risk profile. Note the Threat Check integration, which highlights any IOFA feed matches for rapid validation.

Navigate to the Live Scan tab to initiate a scan. This will yield updated data and a screenshot of the domain’s resolution.
Select Back to DNS List to view all IOCs derived from the article, accompanied by their corresponding risk scores. Organize by severity or category (domains, IPs, URLs).
Select a critical IOC, such as the Quasar domain, and use Save Selected to incorporate it into a new feed. This positions the indicator for platform-based analysis, team dissemination, or SIEM export.
Upon completion, a curated feed of validated indicators will be available for blocking or monitoring purposes.