The Expanded section, accessible via the tabs below Highlights, leverages our domain and enrichment categories to provide granular, pivotable data for advanced threat analysis.
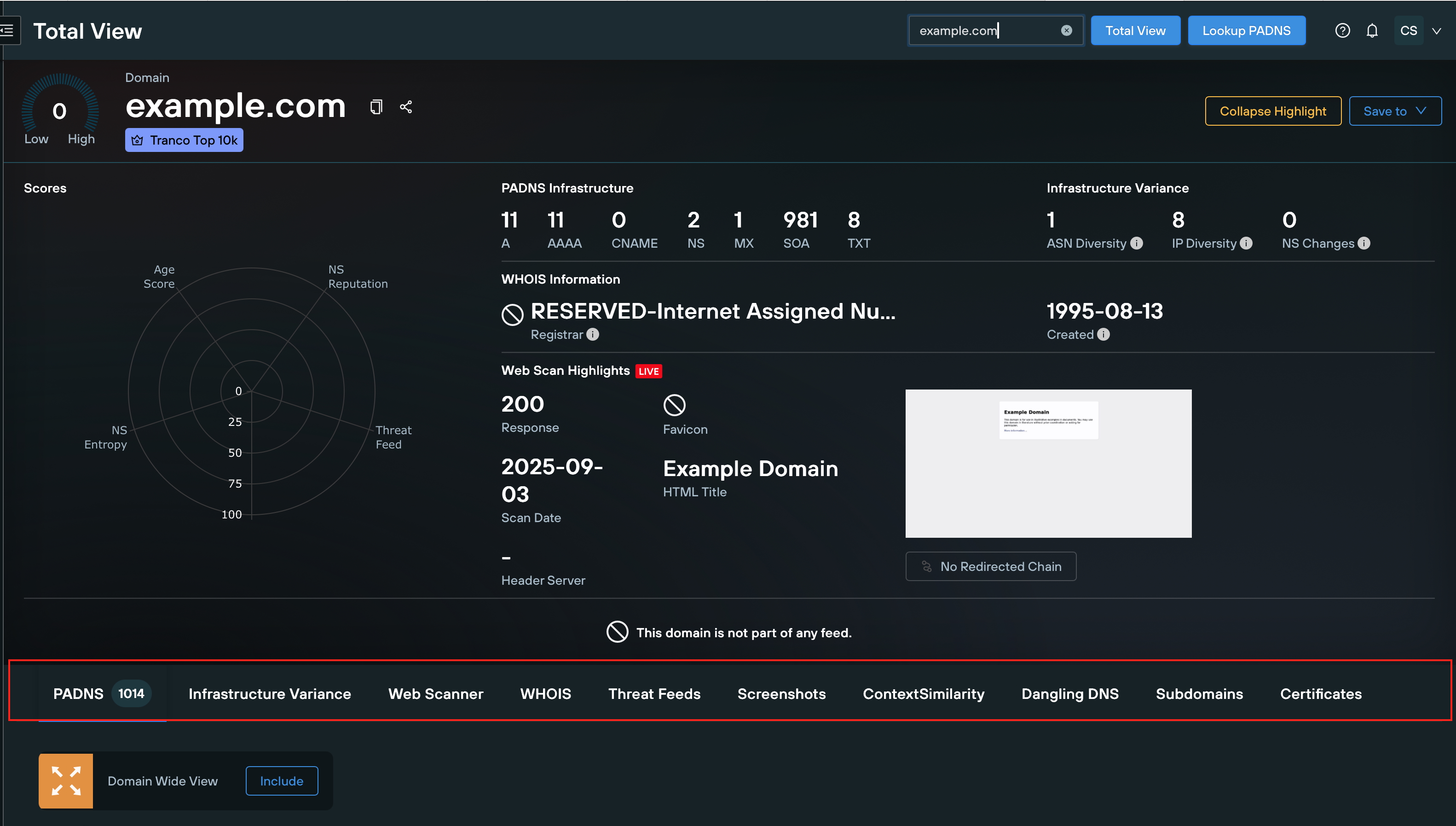
Tab Breakdown
PADNS
Enumerate/DNS records to detect unauthorized changes; pivots on IPs.
Domain enrichment table
Category | Elements | Description |
|---|---|---|
DNS Records | A, AAAA, CNAME, NS, MX, SOA, TXT | Count of DNS records linked to the domain, with a total provided. |
IPv4 enrichment table
Category | Elements | Description |
|---|---|---|
DNS Records | List of recent DNS Records | Recent DNS records with Pivot options, total count displayed. |
Infrastructure Variance
Analyze infrastructure shifts for phishing detection.
Domain enrichment table
Category | Elements | Description |
|---|---|---|
IP Diversity | Host, ASN Diversity, IP Diversity (All), IP Diversity (Groups) | Tracks IPs pointed to over 30 days and ASN changes. |
Nameserver Changes | NS Entropy, Number of Changes, Last Change | Tracks changes in nameservers, including Frequency and recency. |
Nameserver Information | NS Reputation, Nameserver, NS Domain Density, NS Domain Listed | Analyzes nameservers by reputation and domain usage. |
IPv4 enrichment table
Category | Elements | Description |
|---|---|---|
ASN Information | ASN, AS Name, AS Rank, ASN Takedown Reputation, ASN Allocation Age, ASN Allocation Date, ASN Reputation | ASN details, including reputation and takedown responsiveness. |
Subnet Information | Subnet, Subnet Reputation, Subnet Allocation Age, Subnet Allocation Date | Subnet details and reputation. |
Web Search
Extract Scan Data for phishing trait identification; pivot on SSL issuers.
Domain enrichment table
Category | Elements | Description |
|---|---|---|
Certificates | IP, Domains, SHA1, Valid From, Valid Until, Issuer Common Name, Issuer Organization, Scan Date | List of associated certificates. |
JARM | JARM, Scan Date | JARM fingerprint and scan date. |
favicon | Favicon md5, Favicon Murmur3, Favicon2 md5, Favicon2 murmur3, Favicon2 path, Scan Date | Favicon hashes and paths. |
HTML | Body ssdeep, Body murmur3, Title, Scan Date | HTML content analysis. |
Header | Response, Server, Expires, Content Length, Content Type, Cache Control, IP, Location, Scan Date | HTTP Header details. |
IPv4 enrichment table
Category | Elements | Description |
|---|---|---|
Scan data | Same as Domain: Certificates, JARM, Favicon, HTML, Header | Detailed scan data. |
WHOIS
Verifies domain legitimacy with historical data.
Domain enrichment table
Category | Elements | Description |
|---|---|---|
Whois information | Created, Country, City, Address, Email, Zip Code, Registrar | Registration details for the domain. |
Threat Feeds
Prioritizes investigations with real-time data.
Domain enrichment table
Category | Elements | Description |
|---|---|---|
Curated Feed History | Curated Feed History Score First Seen, Listed Recent, Listed Span, Listed All | Scores and timestamps of domain appearances in trusted threat feeds. |
Live Threat Feeds | List of feeds | Current threat feeds featuring the domain. |
IPv4 enrichment table
Category | Elements | Description |
|---|---|---|
Curated Feed History | Curated Feed History Score First Seen, First Seen Ago, Listed Recent, Listed Recent Ago, Listed Span, Listed All | Scores and timestamps of IP appearances in trusted threat feeds. |
Live Threat Feeds | List of feeds | Current threat feeds featuring the IP. |
Screenshots
Visual representation of HTML and Favicon data for threat confirmation.
Context Similarity
Identifies lookalikes.
Domain enrichment table
Category | Elements | Description |
|---|---|---|
Custom Attributes | Customer Domain Score, Top Brand Domain Score, Supplier Domain score | Scores indicating similarity to organizational or Supplier Domains. |
Dangling DNS
Leverages DNS Records for takeover risk assessment (Record Counts all users, Details paid users).
Subdomain
Monitors subdomains with risk scores.
Domain enrichment table
Category | Elements | Description |
|---|---|---|
Basic Information | User Tags, Infratag, FirstSeen, LastSeen, Age, DGA | Tags, infrastructure summary, first/Last Seen dates, Domain Age, and DGA likelihood. |
Certificates
Detects impersonation or expired credentials.
Domain enrichment table
Category | Elements | Description |
|---|---|---|
Certificates | IP, Domains, SHA1, Valid From, Valid Until, Issuer Common Name, Issuer Organization, Scan Date | List of associated certificates. |
Use case
Phishing and malware triage
Scenario: An IP is flagged.
Action: Use Web Search and Screenshots (all users); add Threat Feeds (paid users) for confirmation.
Credential stuffing defense
Scenario: Suspicious login attempts from an IP.
Action: Use IP Context (all users) to filter proxies.
Brand Impersonation detection
Scenario: A retailer suspects a typosquatted domain.
Action: Utilize Subdomains and Web Search (for all users) to identify risks, and add Context Similarity (paid users) for more in-depth analysis.
Manage results
Download data: Use Basic Raw Data or Export (available to all users).
Save queries: Store results in Feeds or Collections (available to all users).
Clear filters: Reset for full visibility (available to all users).